AI adoption in security: Top use cases and mistakes to avoid

AI adoption in security: Top use cases and mistakes to avoid
Widespread implementation of artificial intelligence (AI) in security presents a paradox. On one hand, it helps security experts combat advanced threats at scale. On the other hand, AI is also contributing to the scale of sophistication of adversaries' threat campaigns.
To fight fire with fire, organizations are increasingly automating security processes to make up for the uneven playing field on which they find themselves. In this landscape, AI in cybersecurity is necessary to move from reactive defenses to proactive protection. However, AI adoption isn’t without its challenges and considerations.
This article explores how AI is transforming security operations, the top-value use cases it’s delivering, and key mistakes to avoid when bringing AI into your security operations center (SOC).
How AI is changing cybersecurity
At its core, AI excels at recognizing patterns, learning from vast amounts of data, and making predictions or decisions based on that learning. Together with machine learning (ML) technologies, AI enables advanced data analytics at scale.
For security professionals dealing with an expanding attack surface and advanced threats, AI helps enhance threat detection, automate and accelerate incident response, and improve the accuracy and fidelity of alerts. Its visibility into your data allows for more robust correlation of events, augmenting team productivity for more efficient vulnerability management. This contributes to an overall improvement of organizations’ risk management strategies and processes.
Why AI adoption for security teams is on the rise
Hybrid and multi-cloud environments introduce new vulnerabilities and attack surfaces. Modern attacks are unfolding at unprecedented speeds, traditional systems are generating an overwhelming number of alerts (many of which are false positives), and the industry is operating through a global talent shortage. It’s no wonder that AI adoption is on the rise. In fact, the global market for AI cybersecurity tools is forecast to grow by 27.9% by 2030.
AI helps security teams analyze complex ecosystems more efficiently than manual processes can. AI tools can detect threats, filter alerts, and respond in near real time — minimizing damage to the organization. Ultimately, it acts as a force multiplier, taking on repetitive tasks so that humans can focus on high-value investigations.
Top 5 use cases of AI in cybersecurity
For organizations bolstering their cybersecurity practices with AI, five use cases currently stand out: AI-powered threat detection, SOC automation, incident response, fraud detection and risk analysis, and data onboarding. Let’s dive in.
1. AI-powered threat detection and prevention
Traditional security tools often rely on signatures or known patterns, leaving them vulnerable to novel or evolving attacks. AI, however, can analyze patterns in network traffic, user behavior, and system activities in real time. This enables security teams to identify anomalies that could indicate a breach and means they have equal-strength tools to combat advanced persistent threats (APTs).
Machine learning models are particularly effective at spotting these deviations: Behavior-based detection systems, for instance, can recognize when an insider's actions differ from their usual behavior, flagging a potential threat.
2. AI for SOC automation
When it comes to managing the volume and velocity of data, SOCs are flooded with alerts daily (many being false positives), leading to analyst fatigue and increased vulnerability. AI tools built for security information and event management (SIEM) can now automate threat analysis, distill alerts down to the ones that truly matter, and reduce analyst workload. By using AI within SIEM systems, security teams equip analysts with more focused, high-quality dashboards to guide their daily operations.
3. AI for automated incident response
Incident response requires speed. When analysts are bogged down by data, response times suffer. The longer an attacker lingers within a system, the more damage they can inflict. By automating key threat mitigation steps, organizations can significantly reduce the time from detection to containment, minimizing the need for human intervention.
Security orchestration, automation, and response (SOAR) is a framework that, when powered by AI, can accelerate response automation and escalate critical issues to human analysts only when necessary.
4. AI-driven fraud detection and risk analysis
Sectors like banking, ecommerce, and insurance require robust fraud detection systems. As threats become more advanced and attack surfaces expand, traditional rule-based systems falter, often generating too many false positives and missing more subtle fraudulent behavior. AI-driven fraud detection and risk analysis is an invaluable application of AI in the cybersecurity space.
By analyzing transaction patterns in real time, spotting deviations, and identifying complex fraud tactics that would otherwise go unnoticed, AI and machine learning algorithms help security teams take a proactive stance in their risk mitigation efforts to minimize any potential fraud-related losses.
Octodet proactively prevents threats at the endpoint level and keeps its threat detection capabilities fresh.
5. Data onboarding
AI-powered data onboarding is a game-changer, enabling security admins to ensure their SIEM is operating off a complete, normalized dataset that captures their organization’s entire IT landscape.
By automating custom data integrations, security experts can save weeks of work. What would otherwise take teams days can now be completed in less than 10 minutes by AI, improving the SOC’s ability to get a more holistic view of their environment, faster.
Learn more about the benefits of AI-driven SIEM for your organization.
Common mistakes to avoid in AI adoption for SOCs
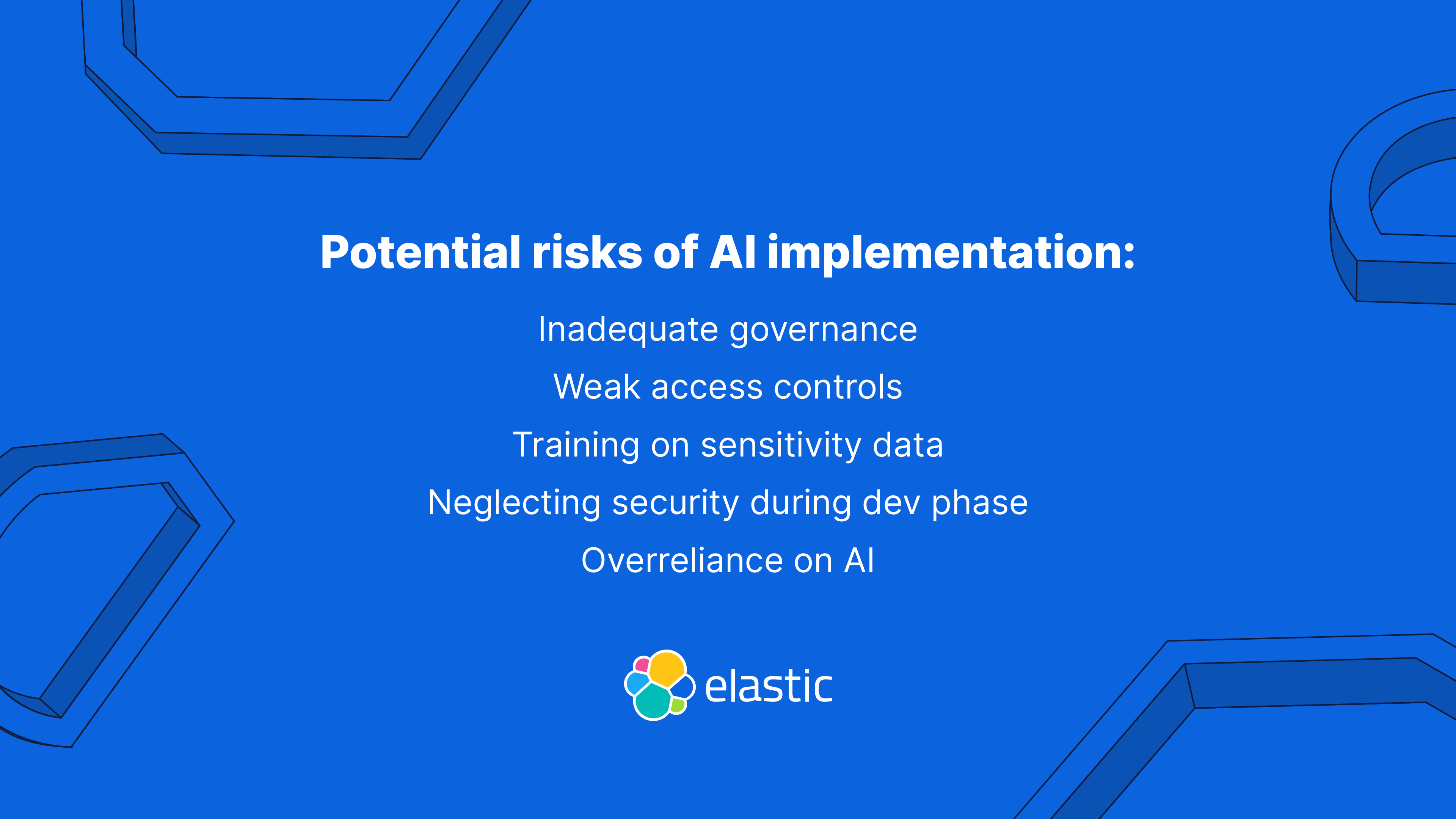
There is a right and wrong way to create an AI-driven SOC. Many organizations make critical mistakes when implementing AI in their security operations. Here are some common implementation pitfalls to avoid:
Inadequate governance: Without proper oversight, AI tools can make incorrect decisions or operate outside regulatory and compliance boundaries, undermining trust among both internal users and external stakeholders. These risks are amplified when there are no clearly established stakeholders overseeing AI adoption.
Without defined roles, responsibilities, and accountability, it becomes difficult to manage AI systems effectively, enforce policies, or respond to incidents when things go wrong. A strong governance framework is essential for ensuring that AI is not only effective but also secure, compliant, and aligned with organizational values.
Weak access controls: AI systems often require access to sensitive data. Without strict access controls, they can become targets themselves. It is imperative to consider security at every step of the adoption process.
Training on sensitive data: Feeding unprotected personal or regulated data into AI models can result in privacy violations and compliance issues. When training models, security teams must identify AI data risks and proceed accordingly.
Neglecting security during development: To prevent malicious tampering, every stage of the development and deployment lifecycle for AI products must factor in security. Especially when implementing opaque technologies like AI, shifting security left in the development process ensures that vulnerabilities are caught early.
Overreliance on automation: AI does not replace human expertise — it augments it. Human oversight remains critical, especially when dealing with context-sensitive threats that AI may misinterpret or miss entirely. To build a productive and efficient AI-augmented security team, organizations must prioritize human judgment in areas like risk evaluation and unexpected system behavior. Collaboration between AI and analysts ensures better decision-making, reduces blind spots, and maintains operational integrity.
Best practices for modernizing your SecOps
There is no one-size-fits-all AI solution. Modernizing your SecOps starts from the ground up by building a foundation that supports the real needs of your security operations team. Successful modernizations are people-centered. They start with a clear understanding of who the technology is serving and how it integrates into daily workflows.
To fully harness the power of AI in your SecOps strategy, consider the following best practices:
Start with a clear strategy: AI adoption should be driven by your organization's specific risk profile and your team’s needs. Begin with well-defined objectives and establish SMART (Specific, Measurable, Achievable, Relevant, and Time-bound) goals for your AI deployment. This ensures you’re solving the right problems and tracking meaningful outcomes.
Invest in data quality: AI is only as good as the data it learns from. Ensure your security tools are fed comprehensive, accurate, and timely data from across your IT environment. Clean, normalized, and enriched data is key to accurate threat detection and effective automation.
Integrate across tools: AI should work seamlessly across your existing security ecosystem — from SIEM to SOAR, endpoint detection and response (EDR), cloud monitoring tools, and beyond. By reducing tool sprawl and enabling unified visibility, this integration improves response times.
Train your teams: Technology is only part of the equation. Training and upskilling empower SOC analysts to understand how AI fits into their workflows, interpret its outputs, and make informed decisions. Human expertise remains critical, especially when navigating edge cases or interpreting AI-driven recommendations.
Monitor and tune continuously: AI is not a “set it and forget it” tool. Regularly evaluate model performance and retrain with updated data. Continuous tuning ensures relevance, accuracy, and trust in your AI systems.
By anchoring your modernization efforts in these best practices, your organization will be better positioned to deploy AI responsibly, improve threat response times, and elevate your overall security posture while keeping your SOC team at the center of the transformation.
Why SOCs choose Elastic Security for AI-driven security analytics
Built on Elastic’s Search AI Platform, Elastic Security integrates advanced AI capabilities into every layer of the SOC workflow. Accelerate data onboarding, get access to more efficient alert triage, and augment the productivity of your security teams with generative AI.
Elastic Security gives you the ability to quiet the noise, focus on what matters, and act fast to defend and secure your organization.
Discover what AI can do for your security operations.
Explore more AI in cybersecurity resources:
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, and associated marks are trademarks, logos, or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.