Uncover the threats buried in your current SIEM and EDR alert noise with Elastic AI SOC Engine (EASE).

Today, we’re excited to introduce the Elastic AI SOC Engine (EASE), an easy-to-deploy package of AI capabilities that cuts investigation time and helps security operations center (SOC) analysts detect complex, hidden threats faster.
Designed for fast adoption, EASE offers a low-friction path to bring AI into your existing security workflows. It’s especially valuable for organizations that can’t yet migrate to a next-gen security information and event management (SIEM) like Elastic Security but still want the power of AI to improve threat detection and investigation.
How EASE helps your SOC
Many SOC teams today rely on SIEM and endpoint detection and response (EDR) solutions that generate valuable alerts but lack mature, built-in AI capabilities to conduct investigations, automatically correlate threats, or reduce noise. As a result, analysts are overwhelmed with high alert volumes and spend hours manually triaging across multiple consoles just to reconstruct the full picture of a threat. This fragmented process leads to slower response times, increasing the window of exposure and risk to the organization.
EASE bridges this gap by integrating with your existing SIEM and EDR platforms. It prioritizes threats and reduces alert fatigue through intelligent, AI-driven alert correlation. The context-aware AI assistant uses your organization’s trusted knowledge sources to provide precise, relevant, and actionable insights customized to your environment while guiding your response workflows. Best of all, you can access these AI capabilities immediately — no migration needed.
Evolve to an AI-driven SOC with EASE
EASE, available as an Elastic Cloud Serverless offering (SaaS), allows analysts to tap into Elastic’s advanced AI capabilities within minutes and enhance existing security workflows with:
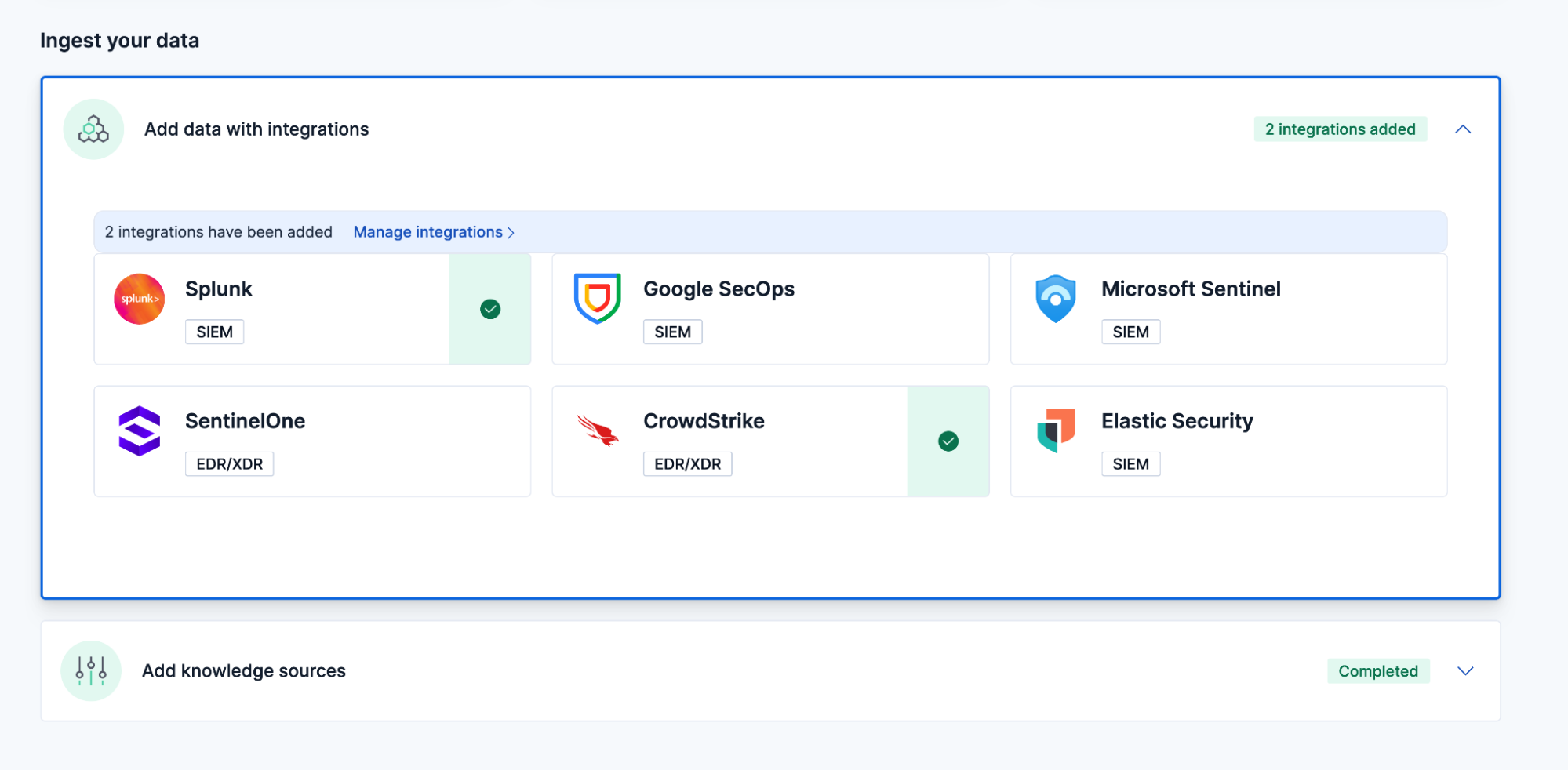
Agentless integration: Native, agentless alert ingestion from third-party SIEM and EDR platforms, including Splunk, Google Security, Microsoft Sentinel, CrowdStrike, SentinelOne, and Elastic Security, allows you to apply AI analysis to your alerts immediately.
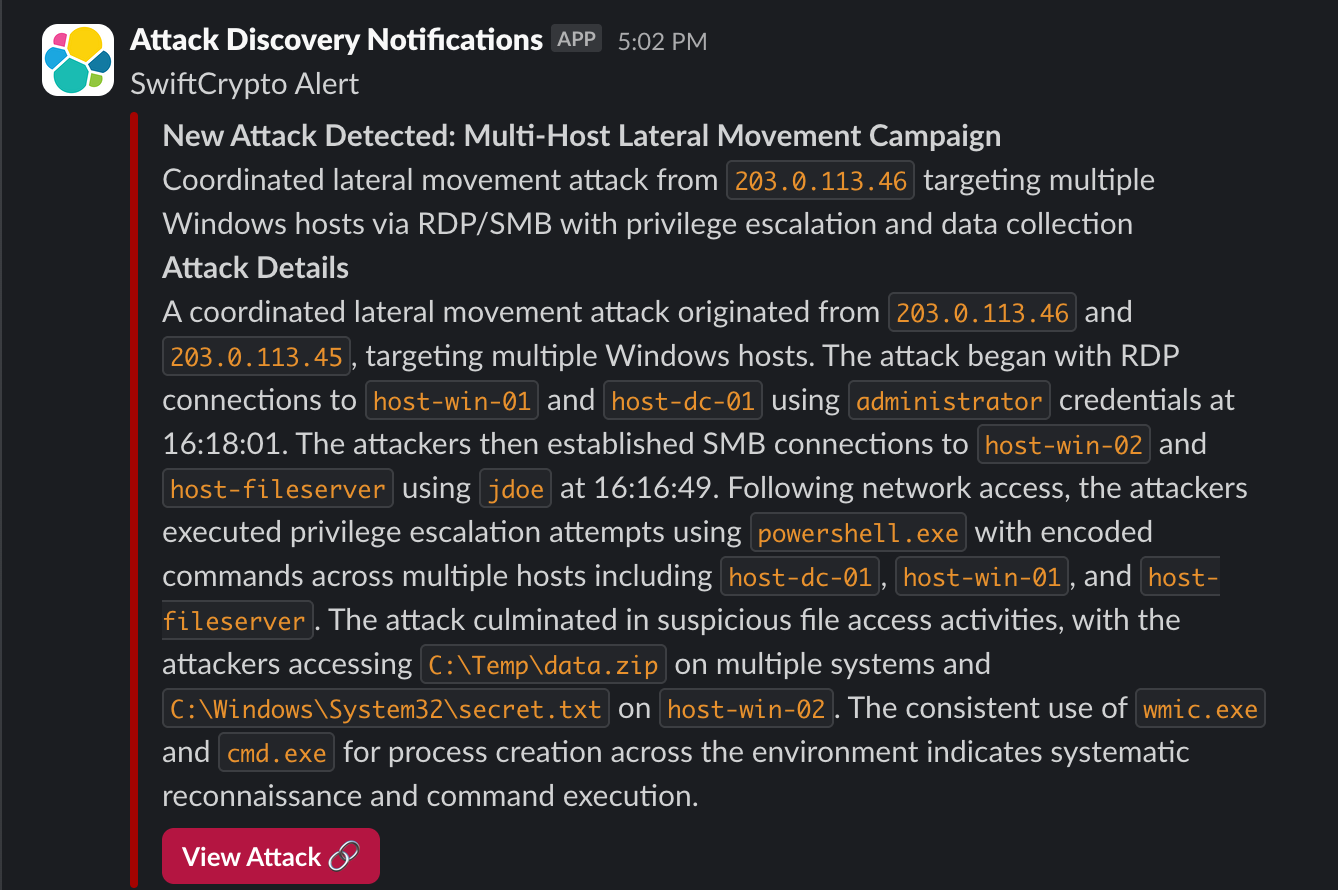
- AI-powered alert correlation: Attack Discovery triages, correlates, and prioritizes alerts with automatic scheduling and real-time notifications for when attacks are discovered. Focused Alert View helps analysts better understand the full scope of an alert instantly by providing AI-powered summaries and context, helping your analysts move from triage to action faster.
- Context-aware AI assistant: Agentless data connectors for GitHub, SharePoint, and JIRA enrich every investigation with your team’s custom knowledge and give AI assistant critical context to provide more accurate, relevant answers. AI assistant supports natural language queries, retrieval augmented generation (RAG)-based search across internal data, Elastic Security Labs content, and more.
- Transparent AI with model flexibility: AI systems should never be a black box, with EASE you can choose the LLM that works best for your organization, either your own, or the Elastic Managed LLM for simplicity. Results from the AI assistant are cited, so it’s clear what data it leveraged to generate an answer. All queries and responses are logged and all consumption tokens can be tracked.
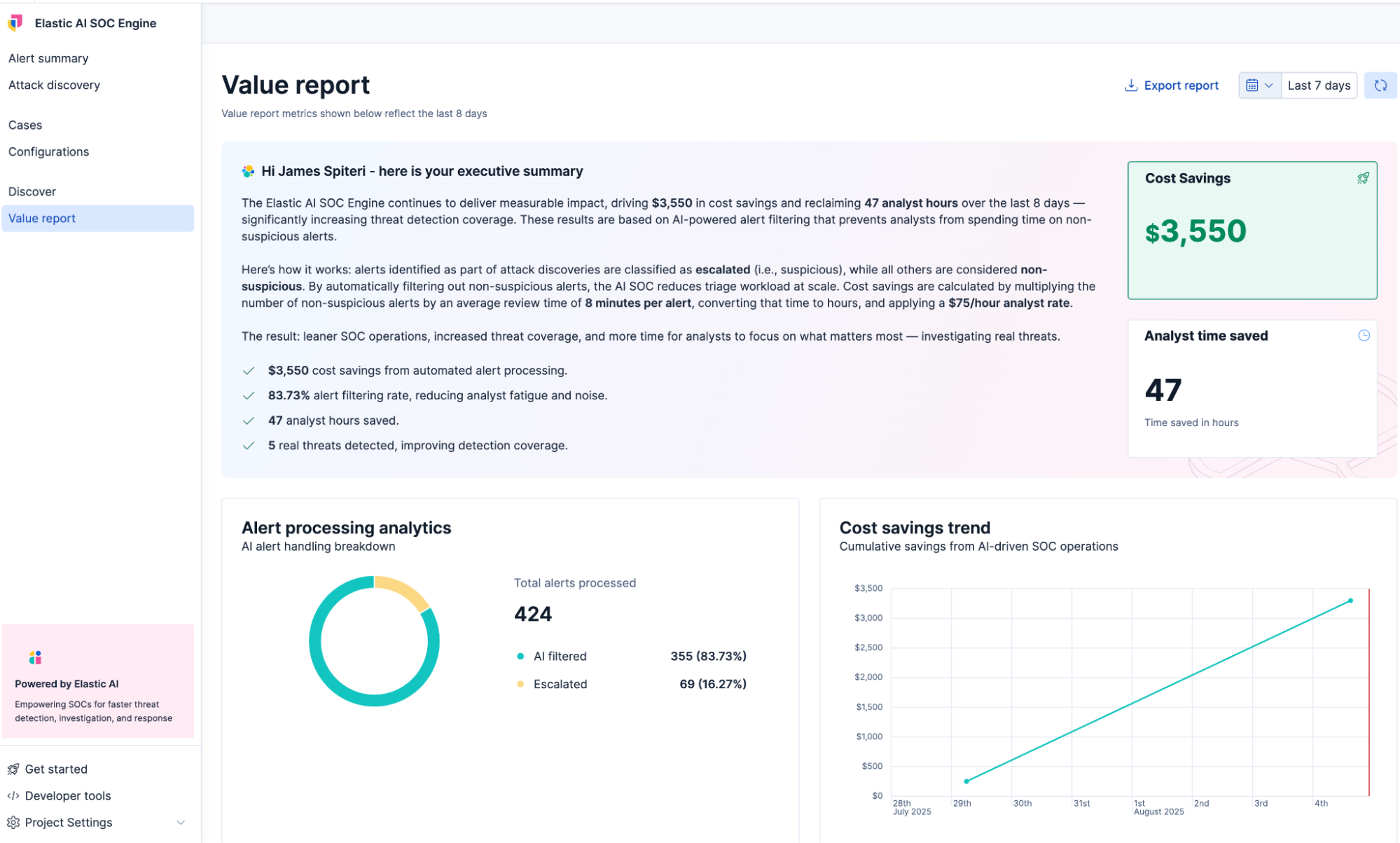
- Operational metrics: Out-of-the-box impact dashboards track efficiency gains and ROI, so you can prove security’s value quantitatively to leadership.
EASE into action: Prioritize and investigate high-risk alerts with AI
Let’s take a look at how you could deploy EASE in your current environment alongside existing third-party security tools to enhance threat investigation.
Using the tailored UX for EASE and agentless API integration, analysts can bring in alerts from their existing SIEM and EDR solutions instantly.
All ingested alerts are presented in a centralized Alert Summary view, where they can be further enriched with AI-driven context that explains why the alert was triggered, the level of risk it represents, and how it connects to broader activity in the environment.
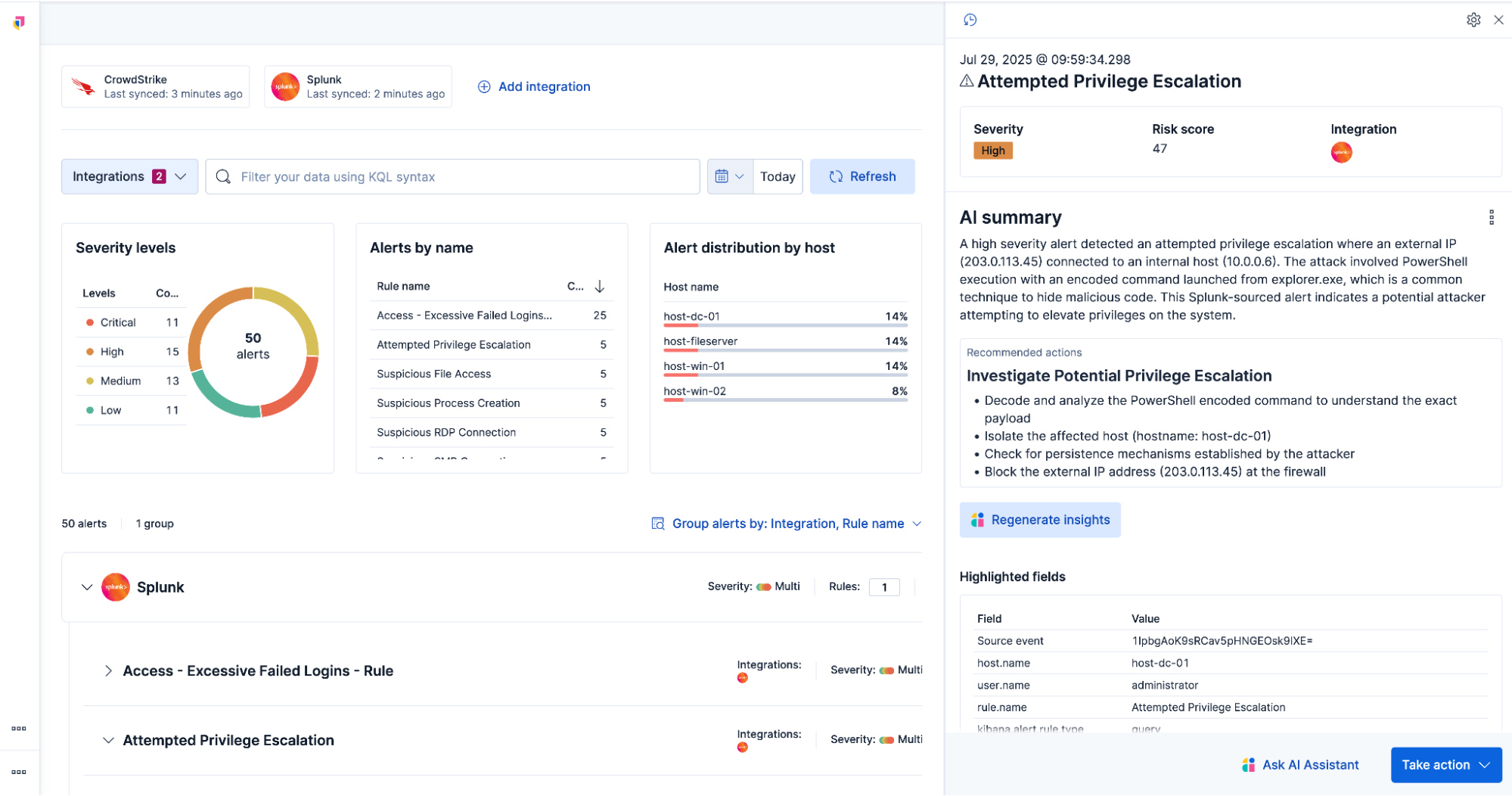
This added context combined with recommended actions helps analysts quickly understand and respond to different types of alerts.
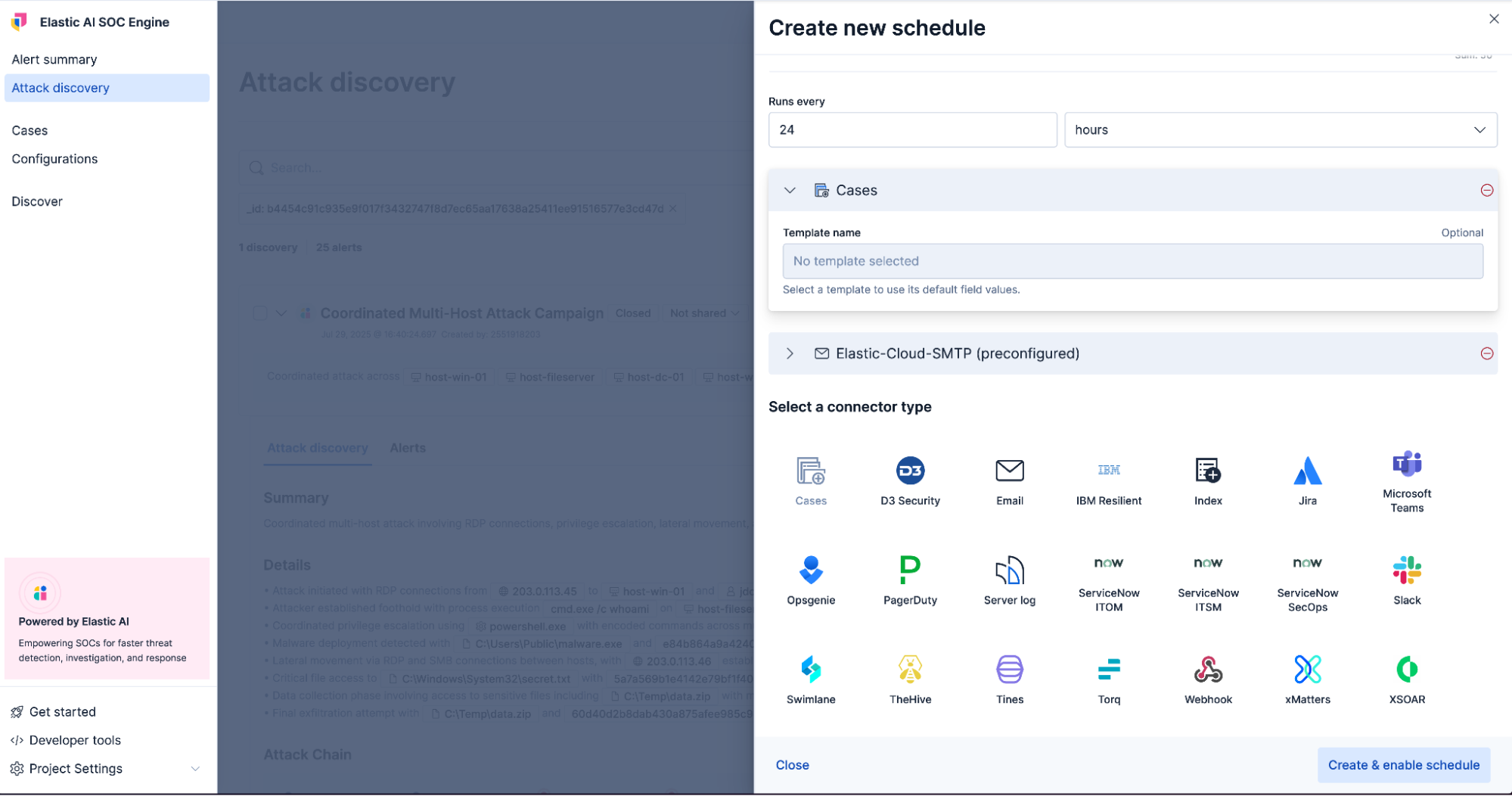
Attack Discovery automatically stitches together alerts to surface broader attack campaigns, helping analysts see the full scope of coordinated activity. Attack Discovery generates a mapped attack chain with a clear summary and detailed views aligned to MITRE tactics and techniques.
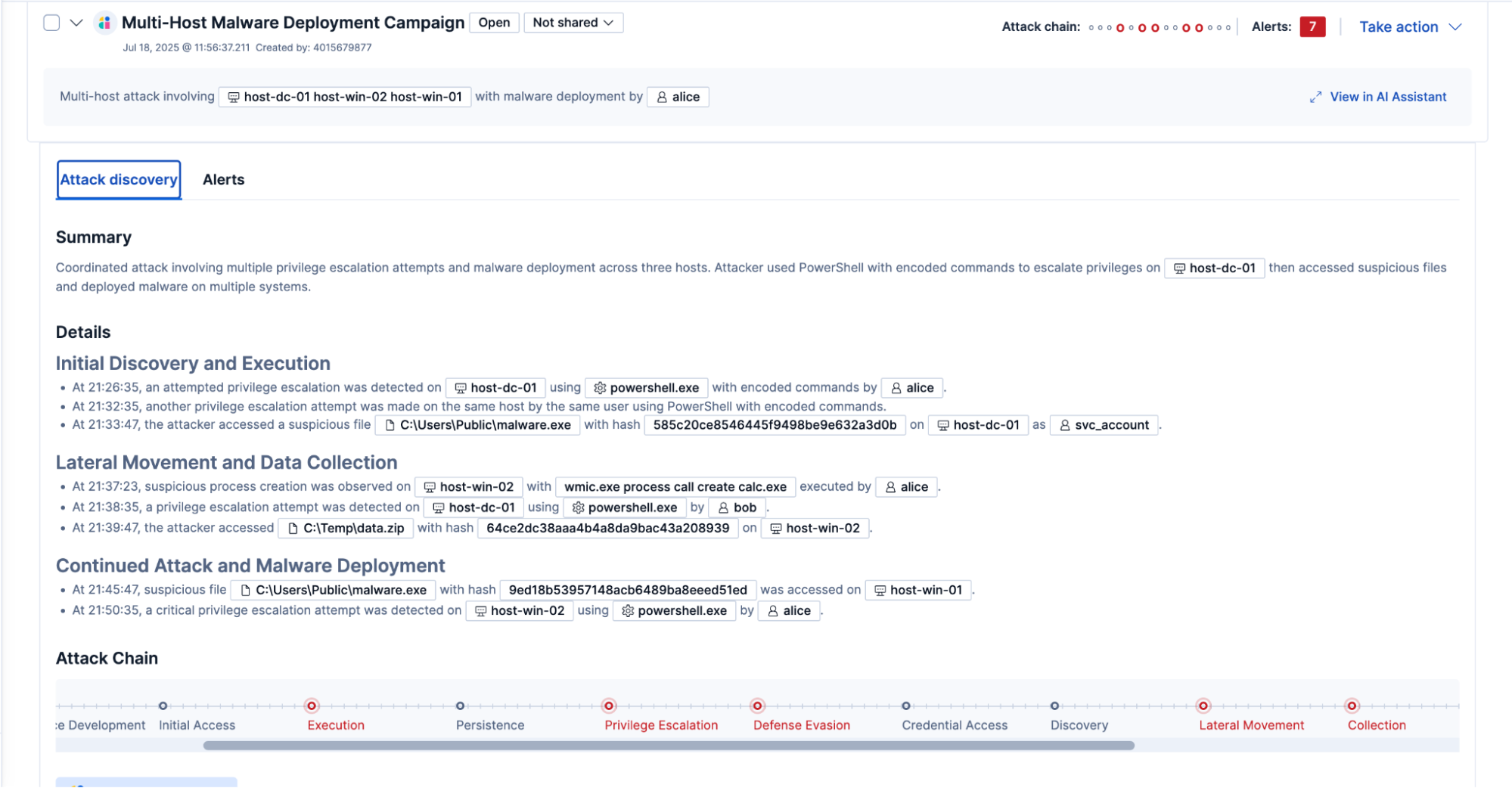
Attack Discovery can be run ad hoc or can be scheduled to run automatically to preemptively uncover threats. Automated response actions, such as firewall blocks or email notifications, can be linked to scheduled discoveries, helping to accelerate threat containment and reduce response time.
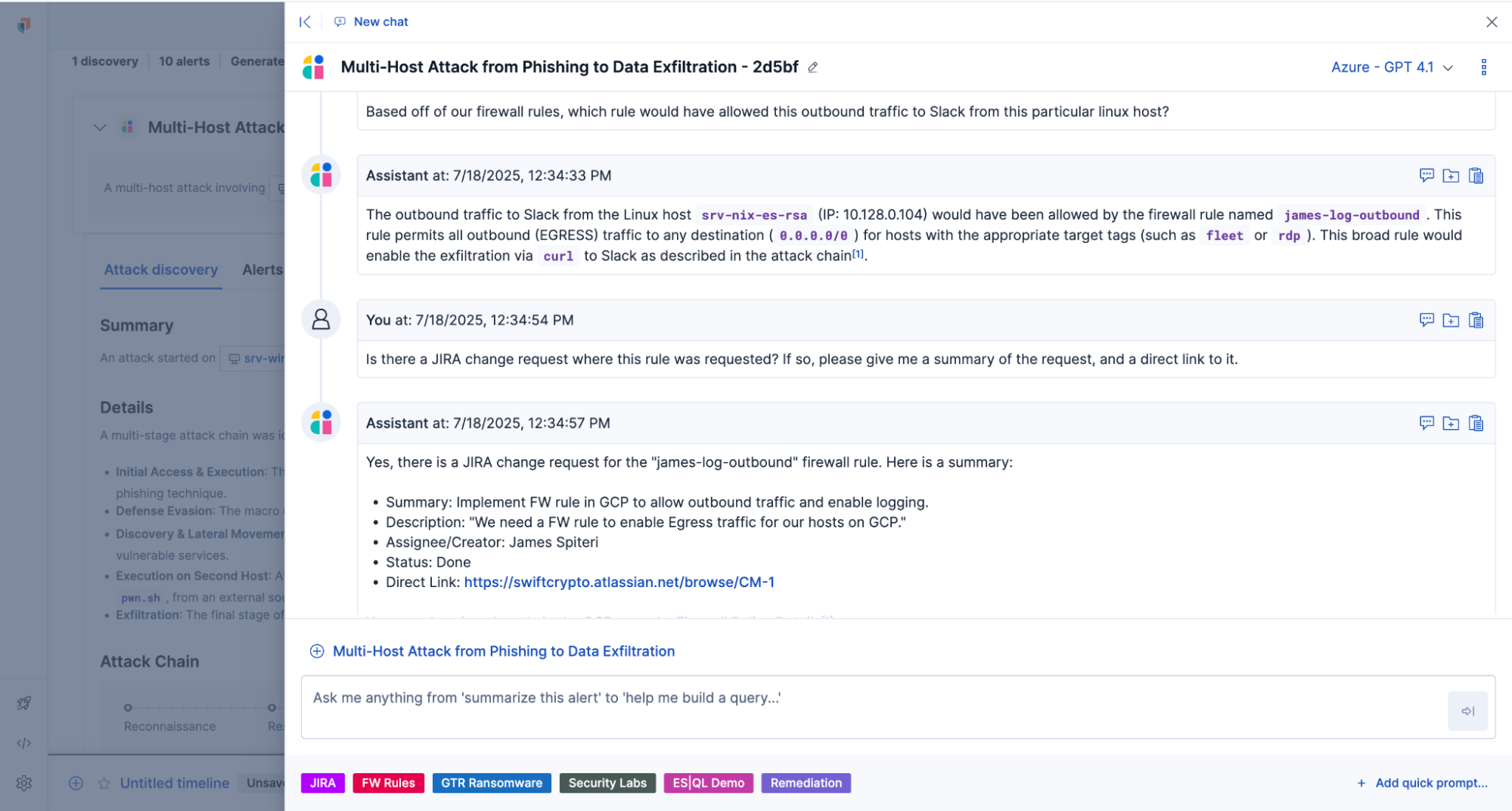
Analysts can invoke Elastic AI Assistant anytime during investigations to retrieve relevant internal knowledge like Jira tickets, KB articles, and playbooks. This reduces manual lookups and speeds up triage decisions.
By integrating EASE with their existing SIEM and EDR environments, the SOC team:
Accelerates alert triage and threat correlation
- Improves detection of complex, coordinated attacks
- Reduces mean time to respond (MTTR)
- Lowers analyst fatigue and increased efficiency
- Enhances security posture without disrupting current investments
Since adopting AI capabilities in Elastic Security, Proficio has increased SOC efficiency by 50%, has cut investigation time by 34%, and is on track to save $1 million over three years.
When you’re ready: A simple path to full Elastic Security
EASE offers customers a simple and quick path to adopt AI capabilities today that integrate with their existing SIEM or EDR. And when the time is right, organizations can move entirely to Elastic’s open, AI-driven SIEM — with all the same AI capabilities of EASE — eliminating the need to maintain two systems.
Elastic Security is an open source, AI-driven solution that unifies SIEM, extended detection and response (XDR), and cloud security — all in one powerful platform. In the recent Forrester Wave™: Security Analytics Platforms, Q2 2025, Elastic was recognized as a Leader with recognition in engineering-led innovation, open and flexible architecture, and breakthrough in generative AI.
The chart below shows the capabilities available in EASE versus Elastic’s next-gen SIEM.
| Feature Category | Feature | Elastic AI SOC Engine (EASE) | Elastic Security Analytics Complete |
| AI SOC Automation | Bring your own LLM | ✓ | ✓ |
| LLM Anonymization and Redaction | ✓ | ✓ | |
| Agentless SIEM and EDR integrations | ✓ | ✓ | |
| Access to Elastic Managed LLM | ✓ | ✓ | |
| Attack Discovery | ✓ | ✓ | |
| Elastic AI Assistant for Security | ✓ | ✓ | |
| AI Value Reports | ✓ | ✓ | |
| Automatic Migration | ✓ | ||
| Automatic Import | ✓ | ||
| Automatic troubleshooting | ✓ | ||
| Core SIEM | Ad-hoc investigations (Discover) | ✓ | ✓ |
| Lightweight alert triage | ✓ | ||
| Advanced alert triage, insights, and investigation | ✓ | ||
| Threat hunting workflows | ✓ | ||
| Threat intelligence integration | ✓ | ||
| Asset Inventory | ✓ | ||
| Prebuilt machine learning detection models | ✓ | ||
| 400+ prebuilt and customizable integrations | ✓ | ||
| Prebuilt findings/dashboards/reports | ✓ | ||
| Customization dashboards/reports | ✓ | ||
| Elastic Security Labs prebuilt detection rules | ✓ | ||
| Advanced Analytics | Customizable prebuilt detection rules | ✓ | |
| Threat intelligence management | ✓ | ||
| Advanced analytic models (UEBA) | ✓ | ||
| Risk-based prioritization | ✓ | ||
| Entity analytics and investigation | ✓ | ||
| XDR | Endpoint protection (optional) | ✓ | |
| Cloud security (optional) | ✓ | ||
| Agnostic endpoint experience | ✓ | ||
| Response and Automation | Cases | ✓ | ✓ |
| Lightweight actions | ✓ | ✓ | |
| Advanced actions | ✓ | ||
| Bi-directional actions | ✓ |
Get started with EASE
Whether you’re looking to adopt Elastic to modernize your SIEM today or evolve from your current SIEM at your own pace, Elastic provides you that flexibility. Ready to see it in action? Start your free trial today and experience firsthand how Elastic AI can help your security analysts.
Want to know what’s included in your trial?
- During the free trial
- Full access to EASE and all AI features like Attack Discovery and the Elastic AI Assistant for Security
- Elastic Managed LLM for the best EASE experience
- After the free trial
- No additional charges beyond your existing data ingest/storage during the trial
- After public preview
- After the public preview, pricing will be usage-based with plenty of notice before it begins.
Want to learn more? Explore the EASE web page for additional details and resources, and visit the EASE docs page to learn how to create your own EASE Serverless project.
Attend our upcoming webinar AI without borders: Extending analyst capabilities across the modern SOC to learn more about our AI capabilities. Register here!
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, and associated marks are trademarks, logos, or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.