What’s new in 8.19
editWhat’s new in 8.19
editHere are the highlights of what’s new and improved in Elastic Security. For detailed information about this release, check out our release notes.
Other versions: 8.18 | 8.17 | 8.16 | 8.15 | 8.14 | 8.13 | 8.12 | 8.11 | 8.10 | 8.9 | 8.8 | 8.7 | 8.6 | 8.5 | 8.4 | 8.3 | 8.2 | 8.1 | 8.0 | 7.17 | 7.16 | 7.15 | 7.14 | 7.13 | 7.12 | 7.11 | 7.10 | 7.9
Generative AI enhancements
editUse Elastic Managed LLM in Security AI Assistant
editElastic Managed LLM is now the default large language model connector in AI Assistant. It gives you immediate access to generative AI features without any setup or external model integration.
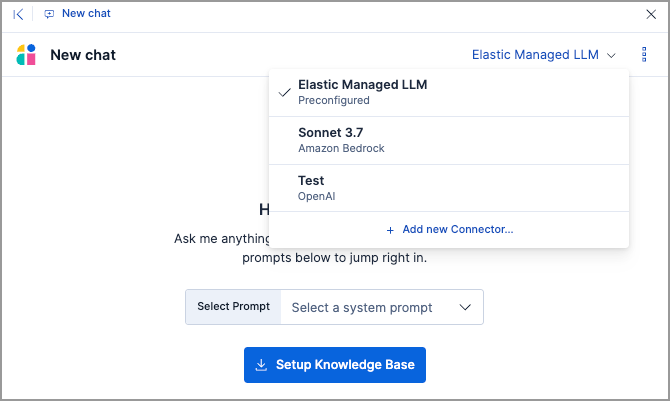
Use prompt tiles in Security AI Assistant
editThe Security AI Assistant's chat UI now uses prompt tiles instead of default quick prompts. Prompt tiles help you begin structured tasks or investigations into common Elastic Security workflows.
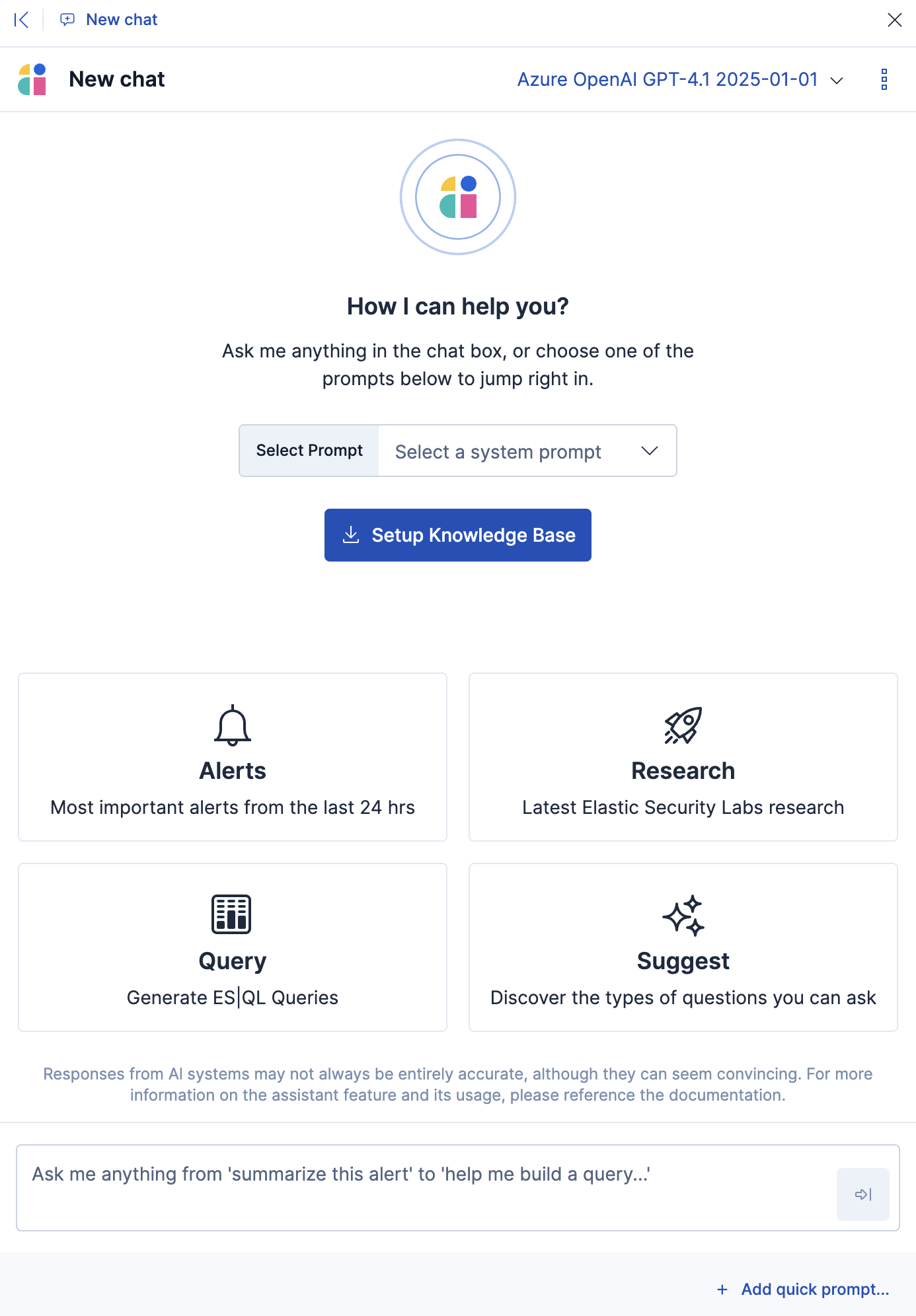
Schedule recurring attack discoveries
editYou can now define recurring schedules to automatically generate attack discoveries without needing manual runs. When discoveries are found, you’ll receive notifications through your configured connectors, such as Slack or email. You can customize the notification content to tailor alert context to your needs.
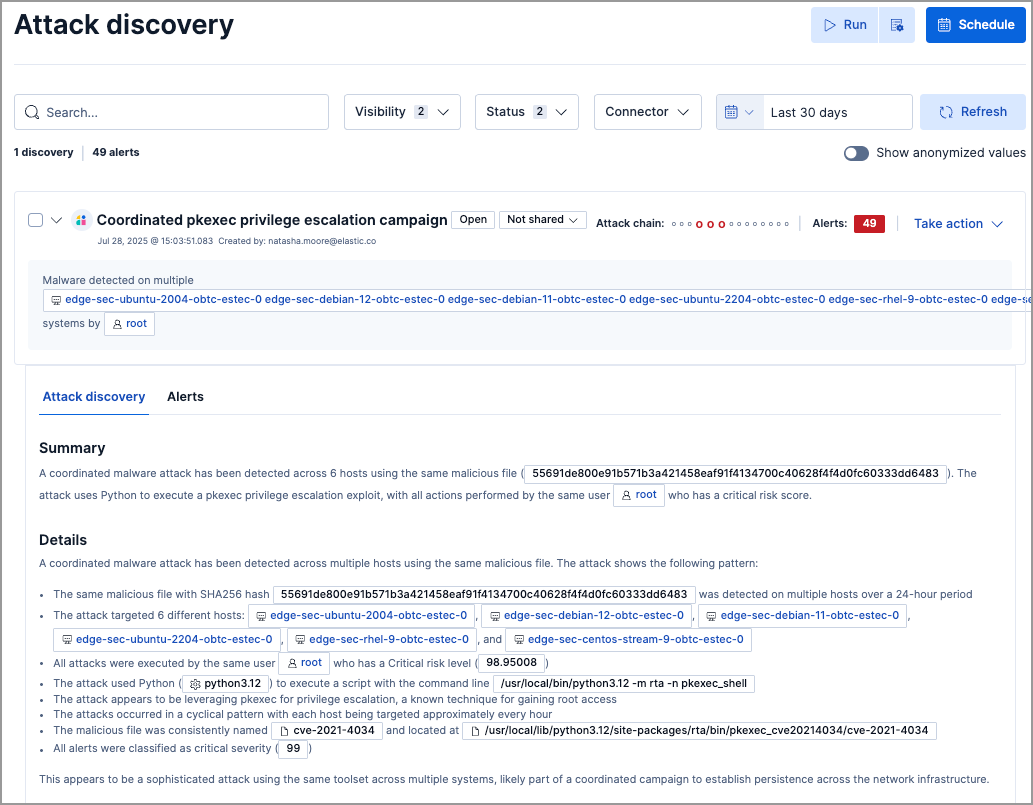
View and manage saved attack discoveries
editAttack discoveries are now automatically saved whenever they’re generated. You can update their status, share manually generated discoveries with other Kibana users, and perform bulk actions, such as status changes or adding discoveries to cases. Use the search box and filters to quickly find relevant discoveries.
Automatic Migration is generally available
editAutomatic Migration is moving from technical preview to general availability. Use this feature to quickly convert SIEM rules from the Splunk Processing Language (SPL) to the Elasticsearch Query Language (ES|QL).
Detection rules and alerts enhancements
editRevert a customized prebuilt rule to its original version
editAfter modifying a prebuilt rule, you can restore its original version. To do this, open the rule’s details page, click All actions → Revert to Elastic version, review the modified fields, then click Revert. The original rule version might be unavailable for comparison if you haven’t updated your rules in a while.
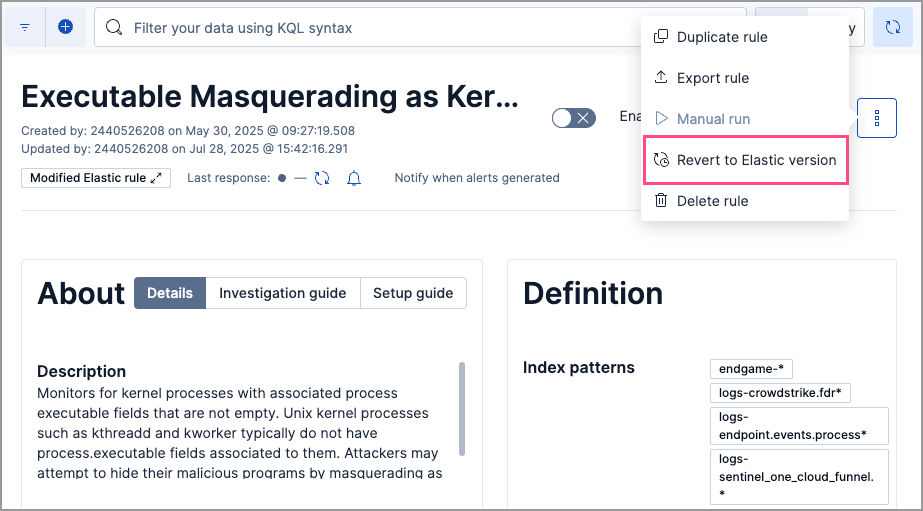
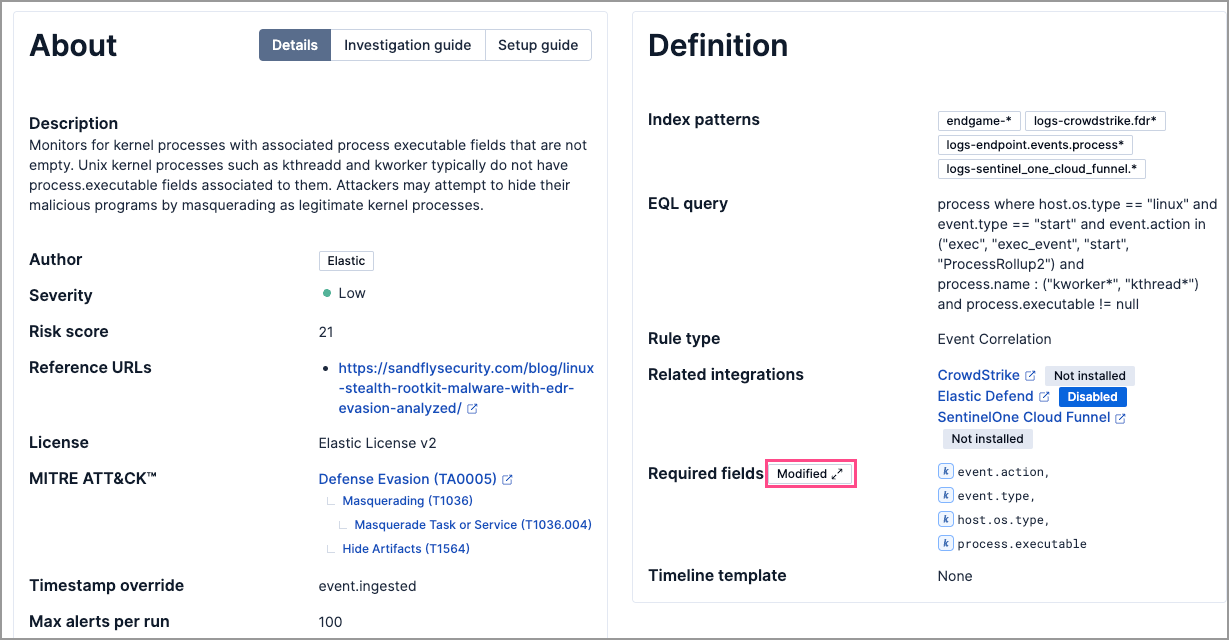
Modified fields on prebuilt rules are marked with a badge
editModified fields on prebuilt rules are marked with the Modified badge on the rule’s details page. You can compare the original Elastic version and the modified version of the field by clicking on the badge.
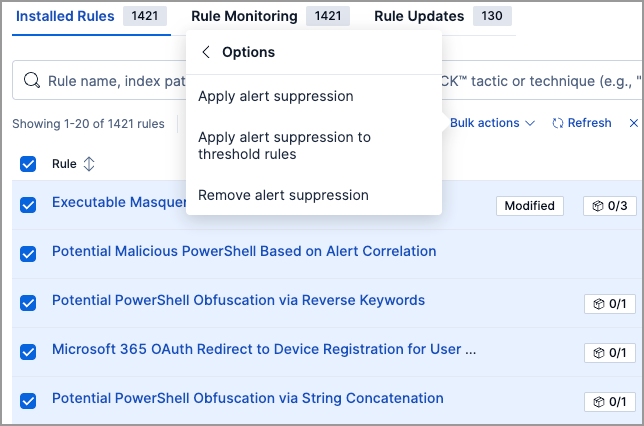
Bulk-apply and remove alert suppression from rules
editFrom the Rules table, use the Bulk actions menu to quickly apply or remove alert suppression from multiple rules. Note that threshold rules have a dedicated option for bulk-applying alert suppression.
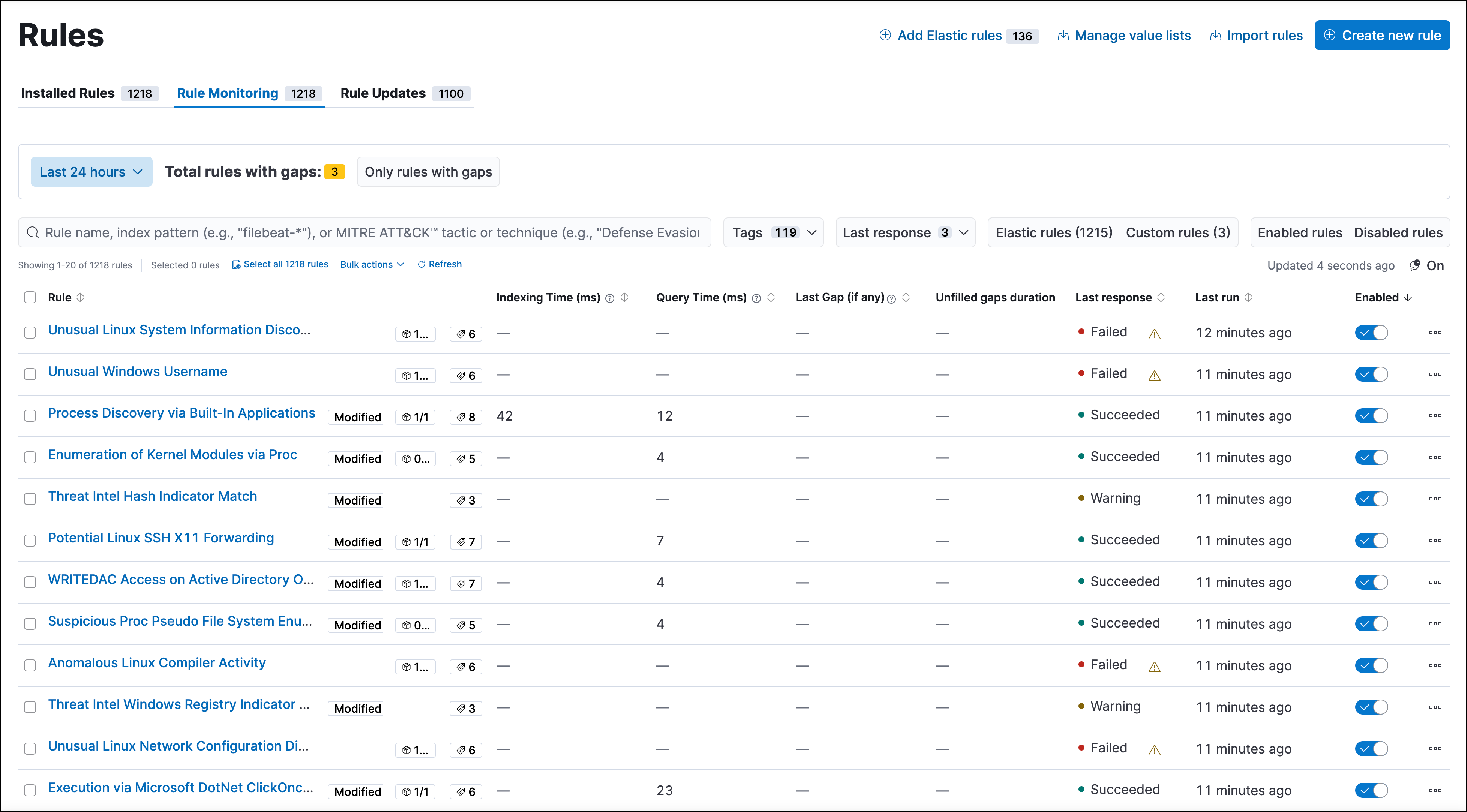
Improvements to gap fills
editSeveral enhancements have been made to the gap fill feature:
- The Gaps table is now generally available and provides you with an option to fill all gaps for a rule.
- In the panel above the Rules table, the Total rules with gaps field now shows how many rules have unfilled gaps and how many are currently having their gaps filled. The Only rules with gaps: filter has also been renamed to Only rules with unfilled gaps: and now only shows rules that have unfilled gaps. Rules with gaps that are being filled are excluded from the filter results.
- You can now bulk-fill gaps for multiple rules.
Response actions enhancements
editRun a script on Microsoft Defender for Endpoint-enrolled hosts
editUsing Elastic’s Microsoft Defender for Endpoint integration and connector, you can now run a script on Microsoft Defender for Endpoint-enrolled hosts.
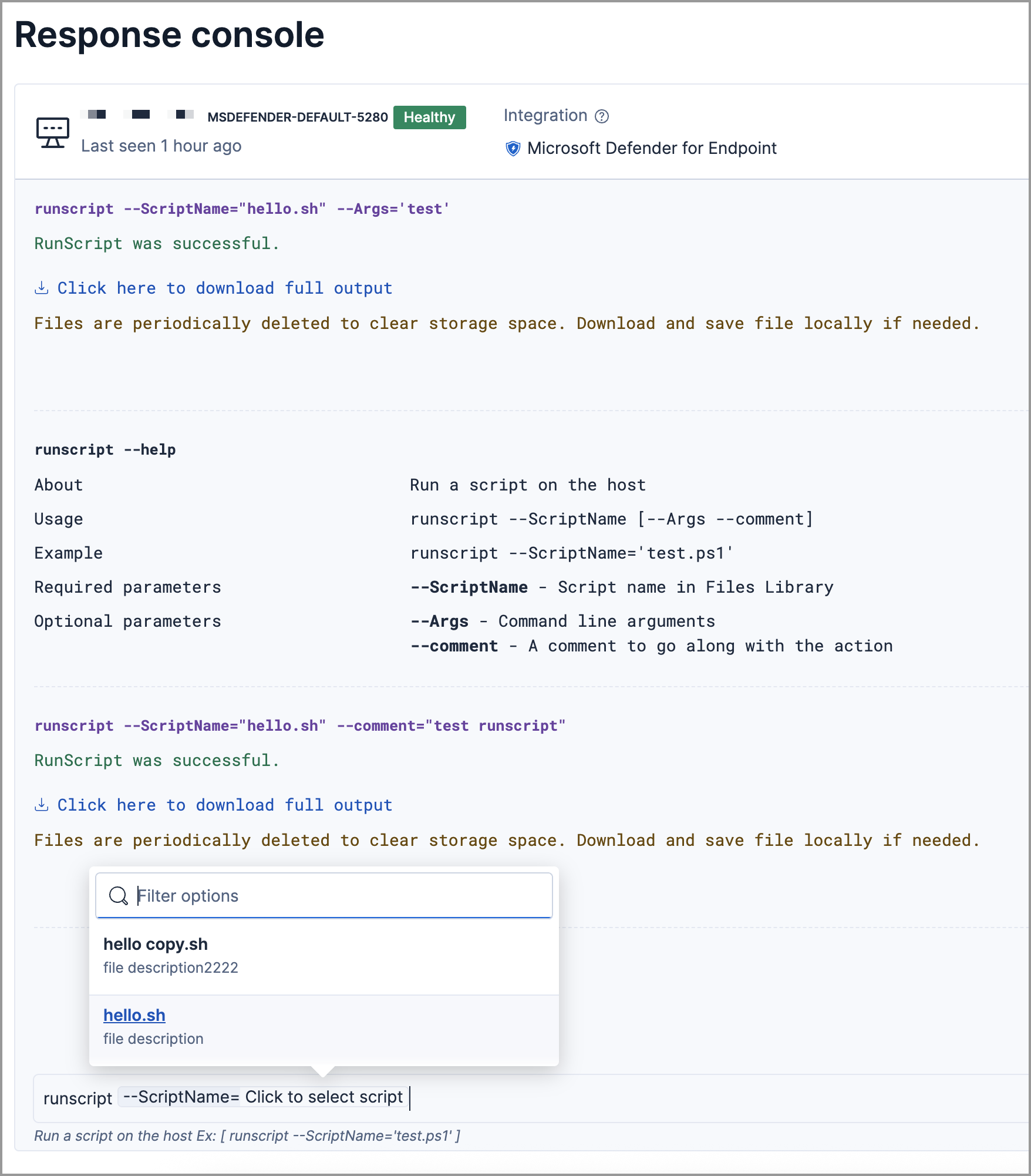
Select saved scripts when using runscript third-party response actions
editWhen using the runscript response action with hosts enrolled in CrowdStrike and Microsoft Defender for Endpoint, you can now select from a list of saved custom scripts. This means you no longer need to type the script name manually.
Investigations enhancements
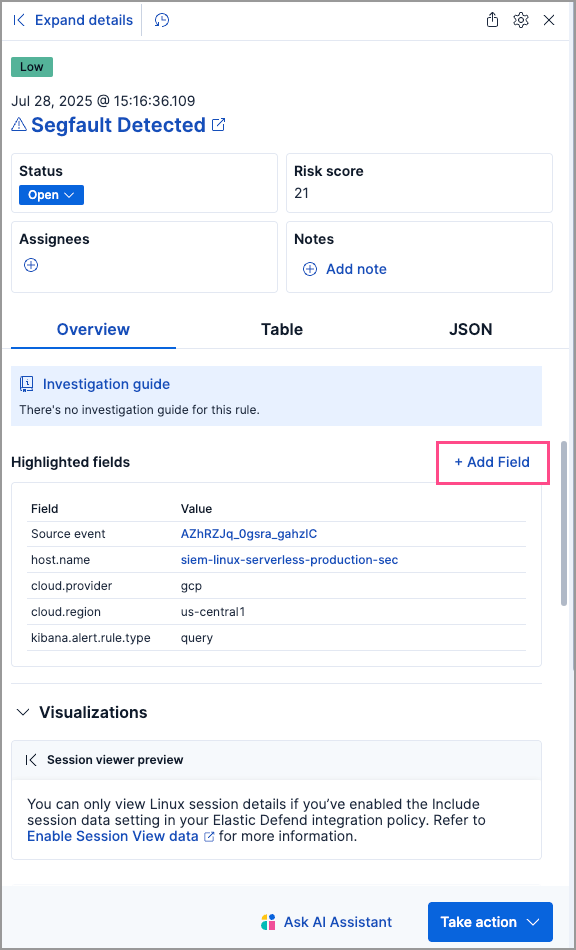
editCustomize highlighted fields for alerts
editYou can now add more fields to an alert’s highlighted fields to display information that’s relevant to your investigations.
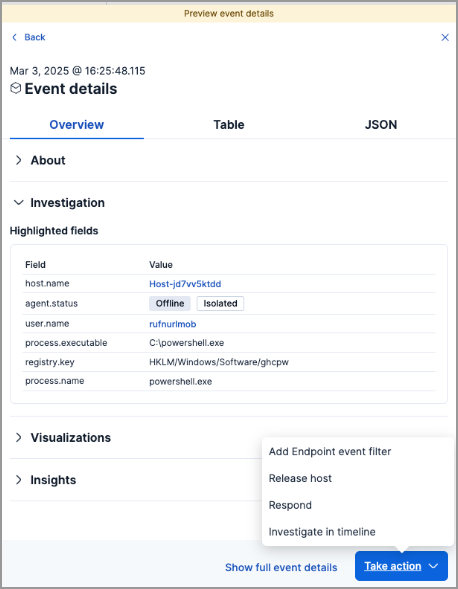
Access the response console from events
editNow, you can access the response console from events, giving you more places to use response actions. You can now also isolate or release a host from events.
Cloud Security enhancements
editNew integrations
editElastic Security now supports three new Cloud Security integrations: Rapid7 InsightVM, Tenable Vulnerability Management, and Qualys VMDR.